Post-Quantum Cryptography
Cornerstone for Security in the Coming Quantum Computing Era
Lily Chen
Mathematician, Cryptographic Technology Group
National Institute of Standards and Technology
Sponsored by PSW Science Member Frederica Darema
About the Lecture
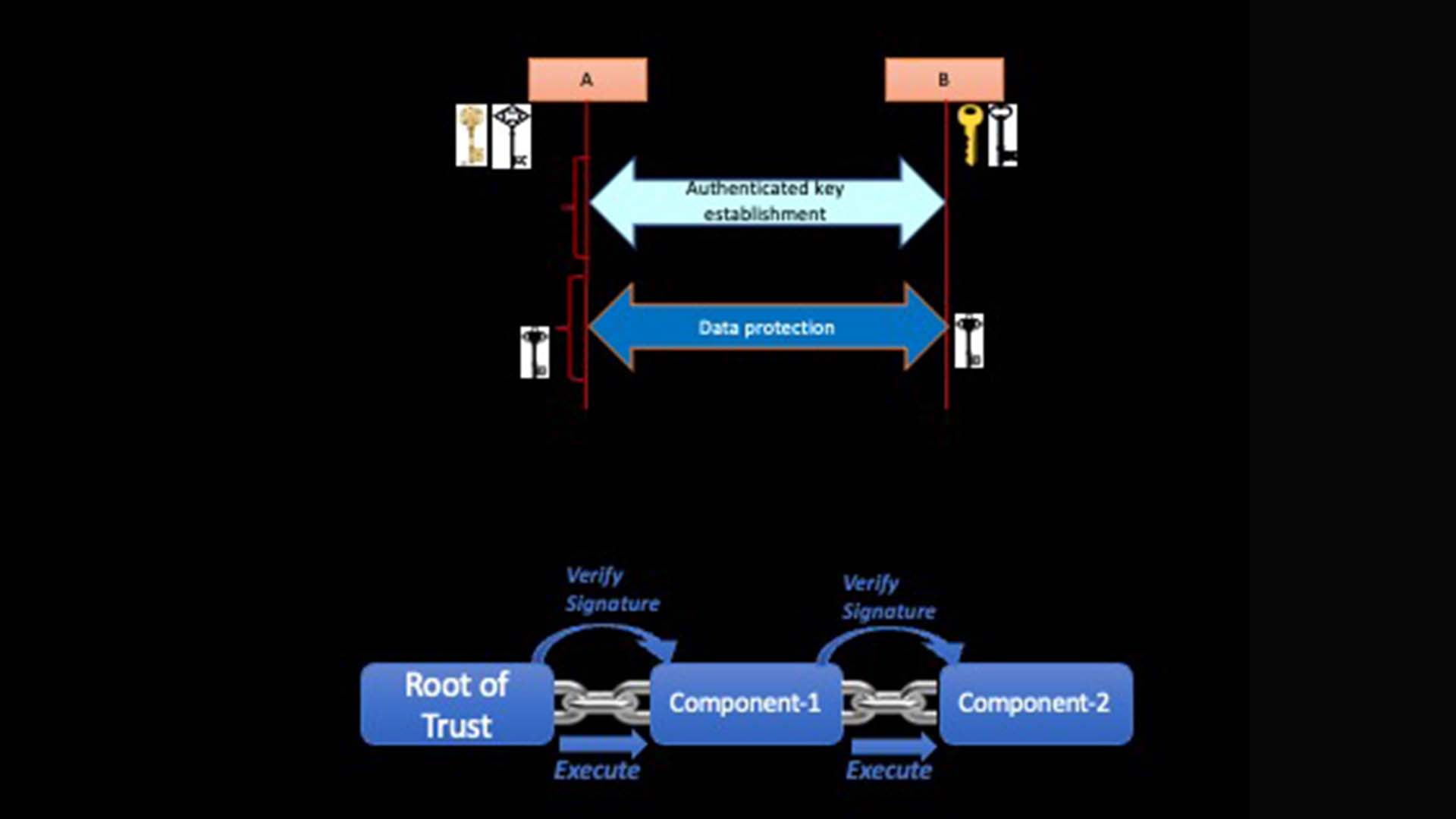
Cryptography is the cornerstone and foundation of cybersecurity. Public-key cryptography has been deployed successfully to secure communications and establish trusted platforms. However, quantum computers have the potential to undermine current cryptographic defenses.
This lecture will introduce efforts to develop quantum resistant cryptography, post-quantum cryptography, and it will focus on efforts at the National Institute of Standards and Technology (“NIST”) to develop cryptographic standards for the quantum era.
The presentation will highlight challenges in standardizing post-quantum cryptography and will discuss strategies for transition to and adoption and adaption of quantum resistant cryptographic methods and standards.
Selected Reading & Media
Reference: https://nvlpubs.nist.gov/nistpubs/ir/2016/NIST.IR.8105.pdf
About the Speaker

Lidong (Lily) Chen is a mathematician and heads the Cryptographic Technology Group in the Computer Security Division, NIST. She leads the development of cryptographic standards published in Federal Information Processing Standards and NIST Special Publications.
Lily has more than thirty years of experience in cryptographic research and applications with academic, industry, and government. Her areas of research include cryptographic protocols, zero-knowledge proof, special featured digital signature schemes, network security, and security for wireless and mobility. She has actively contributed to cryptography and security standards development by the IEEE, ISO, and other standards organizations, as well as NIST.
She is an author on numerous technical publications and a co-author of the textbook Communication System Security, now in use at many universities.
Among other honors and awards Lily received the Silver Medal Award of the Department of Commerce and a Federal 100 Award.
Lily earned a PhD in Applied Mathematics at Aarhus University, Denmark.
Minutes
On January 20, 2023, from the Powell Auditorium of the Cosmos Club in Washington, D.C, and by Zoom webinar broadcast on the PSW Science YouTube channel, President Larry Millstein called the 2,470th meeting of the Society to order at 8:01 p.m. ET. He welcomed new members, and the recording secretary read the minutes of the previous meeting.
President Millstein then introduced the speaker for the evening, Lily Chen, a mathematician who heads the Cryptographic Technology Group in the Computer Security Division at the National Institute of Standards and Technology, or NIST, where she leads the development of cryptographic standards.
Her lecture was titled, “Post-Quantum Cryptography, Cornerstone for Security in the Coming Quantum Computing Era”
The speaker began by introducing NIST as a research institute which has produced 5 Nobel prize winners and pointing out that NIST has been involved with Cryptographic standards since the 1970’s.
Chen continued by discussing the differences between cryptography and encryption by reviewing the fundamentals of Symmetric-key cryptography. Security of encryption is based on a key shared by two communicators and the authentication algorithm is public. In world War two, the speaker explains, this key was distributed through secret channels.
The need for a secret channel was removed in the 1970s with the invention of public-key cryptography. Shortly thereafter, in 1978, a paper establishing the RSA encryption method based on factorization was published. This method is still being used today to assist in establishing this public key cryptography to secure communications.
Chen then moved on to discuss the relationship between research, standards, and applications of quantum cryptography.
Cryptography is a research area, Chen explains, so only mature methods inform standards. The standards apply to security and interoperability of cryptographic methods, as used in internet router communications. Applications of these standards are broken into 4 categories; public key based, tools, symmetric key based, and guidelines for how to use tools and operate using standards.
Chen reviewed some difficulties associated with the math for the keys. And discussed fundamental changes in the field, such as in 1994 when the calculation regime changed after an MIT professor, Peter Schor, created a quantum algorithm which exponentially sped up the computation of factoring large integers.
The speaker then transitioned to discussing the active research area of post quantum cryptography. Thousands of papers have been published in the past decade, Chen points out. Within these papers there are several main categories, in including lattice based, code-based, multivariate, hash or symmetric key-based signatures, and elliptic curve isogeny-based.
Chen then comments that there is a one in five chance that some fundamental public key cryptography will be broken by 2029. She then shows agreement that quantum computers will be able to break RSA-2048 in 28 in approximately 20 years. She concludes that within this timeframe, there should an upgrade to quantum resistant cryptography.
The speaker then discussed the challenges of finding quantum-resistant algorithms and explained that NIST calls for proposals to identify such algorithms. Chen continued by describing the ongoing efforts which have been opened up to participants around the world.
Chen concluded with summarizing a plan to release draft standards for public comments prior to final for the first site of the poster Quantum cryptography will be in 2024.
Next the question and answer period began. One of the members asked about the relationship NIST has with National Security Agency, which has primary
cryptographic responsibility for the military and for intelligence agencies.
Chen responded by noting that NSA and NIST have a different mission. Her work with NIST is an open, world wide effort and the National Security Agency has their own standards and they can not participate in the open procedures.
A question from a member participating through the web asked about the compatibility of the new PQC standards with IPV6. Chen responded that she does not know specifically for the IPV6 but they have tested them with TOS transport.
After the question and answer period, President Millstein thanked the speaker, made the usual housekeeping announcements, and invited guests to join the Society. President Millstein adjourned the meeting at 9:44 p.m.
Temperature in Washington, D.C.: 5° C
Weather: Partly Cloudy
Attendance: Attending in person: 59, concurrent live stream viewers: 39, for a total live viewership of 89, and the number of online viewers in the first two weeks of posting was, 199.
Respectfully submitted,
Cameo Lance, Recording Secretary